Advertiser Disclosure
All About Cookies is an independent, advertising-supported website. Some of the offers that appear on this site are from third-party advertisers from which All About Cookies receives compensation. This compensation may impact how and where products appear on this site (including, for example, the order in which they appear).
All About Cookies does not include all financial or credit offers that might be available to consumers nor do we include all companies or all available products. Information is accurate as of the publishing date and has not been provided or endorsed by the advertiser.
Editorial Policy
The All About Cookies editorial team strives to provide accurate, in-depth information and reviews to help you, our reader, make online privacy decisions with confidence. Here's what you can expect from us:
- All About Cookies makes money when you click the links on our site to some of the products and offers that we mention. These partnerships do not influence our opinions or recommendations. Read more about how we make money.
- Partners are not able to review or request changes to our content except for compliance reasons.
- We aim to make sure everything on our site is up-to-date and accurate as of the publishing date, but we cannot guarantee we haven't missed something. It's your responsibility to double-check all information before making any decision. If you spot something that looks wrong, please let us know.
Everything from streaming apps to web browsers requires a password. But if you have multiple devices and potentially hundreds of logins, that’s a lot of passwords to keep track of.
So how exactly do people create and track their passwords? And how many people are using unsafe password practices that put their digital security at risk? How many different passwords does the average person even use?
To find the answers to these questions, the All About Cookies team surveyed 1,000 U.S. adults about their password habits.
Does the average person use risky password practices?
Password safety
How many people reuse and share passwords
Advice from our experts
Tips for better password protection
Methodology
Key findings
- 84% of internet users have unsafe password practices, such as using birth dates or personal information.
- More than half (52%) of people have five or fewer passwords for all of their logins.
- 45% of people still use a password that is more than 10 years old.
- 50% of people who use shared passwords also use that same password for other accounts.
- 80% of public Wi-Fi users don’t protect their devices.
- 43% of people use passwords that contain the name of a pet or loved one, or a birthday.
Does the average person use risky password practices?
Cybersecurity experts warn against a number of risky behaviors when creating passwords, including discouraging people from reusing the same password for multiple accounts, and from using personal information in their passwords. But how many people actually follow that advice? Turns out, not that many.

Over half of the population (52%) say they have only five unique passwords that they actually use (including small variations). Given how many digital accounts most people have, it seems highly likely that most people reuse the same handful of passwords for most of their accounts.
Still, there are plenty of people who vary their passwords to keep themselves safe. Though the average number of passwords was 12, one in eight respondents said they have at least 25 unique passwords for their online accounts — and 5% said they have at least 50.
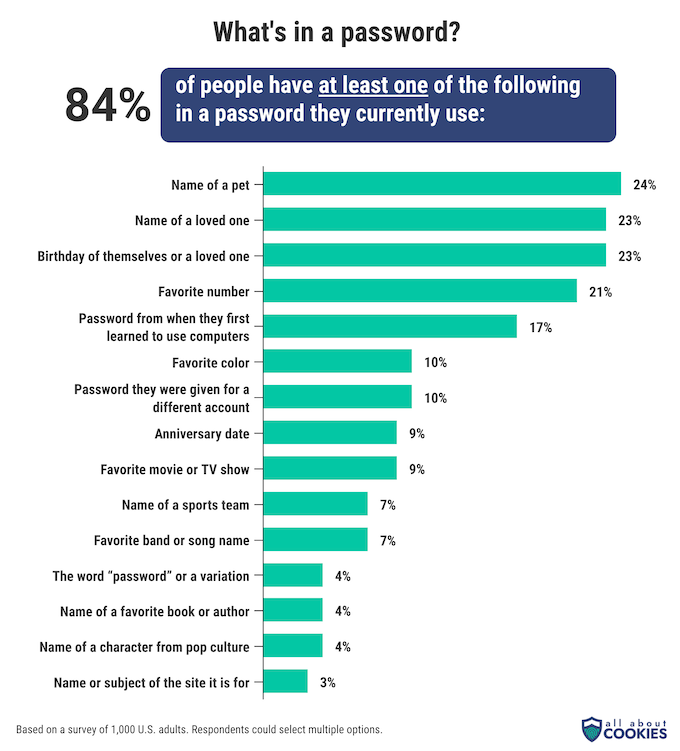
When it comes to keeping personal information out of passwords, nearly everyone falls short of safe standards. 84% of people use at least one unsafe or researchable piece of information in passwords they regularly use.
Nearly one quarter of people use the name of a pet in their passwords. That makes it the most common piece of information people use. More than one in five people said they use the name or birthday of a loved one, their own birthday, or a favorite number when creating passwords.
Password safety
Thanks to hackers and security breaches on high-profile websites, even well-crafted passwords can be exposed. But that doesn’t always make people stop using them.
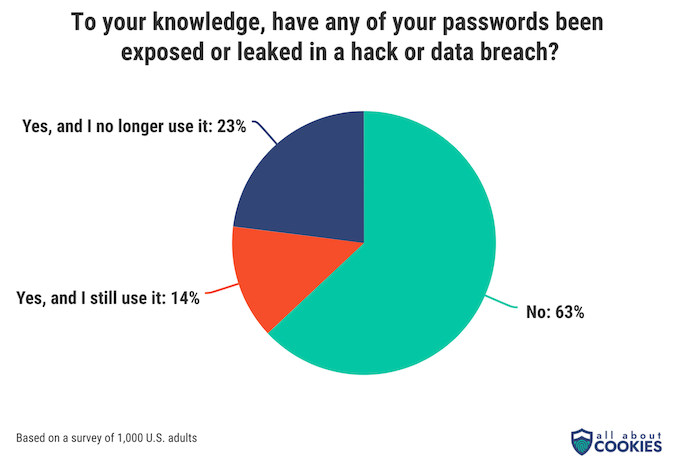
37% of people say they are aware of at least one of their passwords that has been exposed or leaked in a data breach. And while the majority of people don’t use breached passwords anymore, we still found that more than one out of every 10 people (14%) say that they have had a password leaked but still use it anyway.
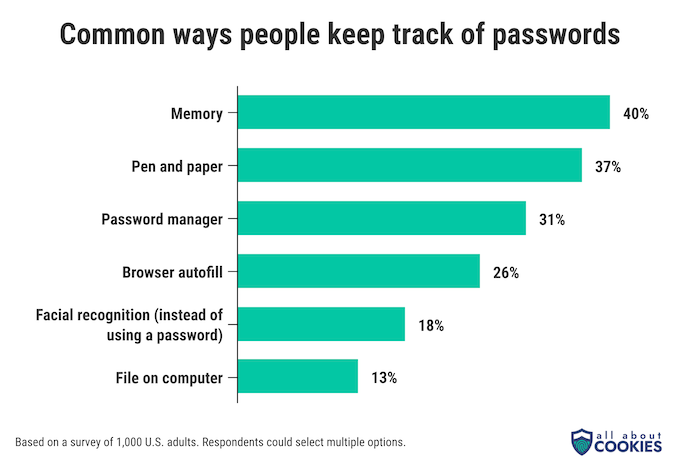
When asked how they track their passwords, the most common method was for people to rely on their own memory — 40% of people claim they do.
Nearly the same percentage of people (37%) say that they write down passwords on something like a note card or piece of paper. And just under one-third of people (31%) use a password manager to track and store their passwords for them.
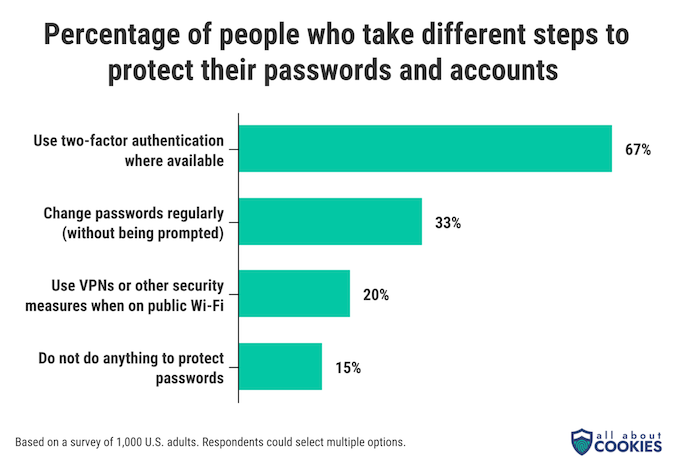
There are steps users can take to keep their devices and passwords secure. When asked about specific cybersecurity measures, a little more than two-thirds of people said they use two-factor authentication whenever it’s available. That’s far and away the most common security step people take.
There are other simple and effective safety measures that most people don’t use. Only one in three people proactively change their passwords without being prompted to do so. And 80% of people eschew things like VPNs when they use their devices on a public Wi-Fi network. Finally, 15% of people claim they do not do anything at all to protect their passwords.
How many people reuse and share passwords
We found that more than half of the population (57%) shares passwords and other login information for at least one of the kinds of accounts shown below.
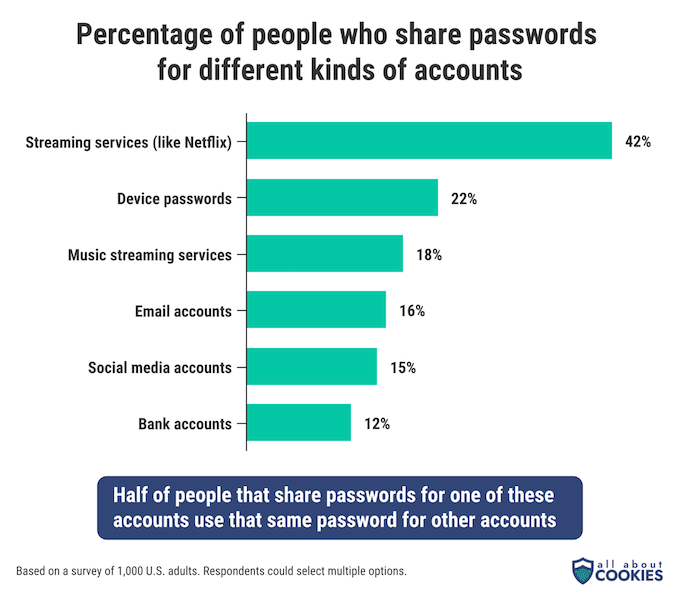
Streaming service passwords are the most commonly shared — 42% of people admit to giving their login information to someone else.
While password sharing can be done safely, you shouldn’t use the shared password for anything else. Unfortunately, 50% of people who share passwords say that the password and/or login information they have shared is the same info they use for other accounts too.
Advice from our experts
Sepideh Ghanavati, Ph.D.
Assistant Professor of Computer Science — School of Computing and Information Science
University of Maine
How often should people change their passwords to ensure they are protected?
Unlike most common practices, research has shown that changing passwords frequently may result in weaker passwords or reuse of passwords. Hence, NIST (the National Institute of Standards and Technology) does not recommend changing passwords frequently. The best guideline is to change [your password] when there is a breach, or every 365 days. In addition, NIST recommends having lengthier passwords rather than complex ones with special characters. Hints for passwords should also be avoided.
What are some best practices for people to avoid getting their passwords compromised or leaked?
Nowadays, having only single-factor authentication makes people highly susceptible to breaches or compromise. First and foremost, people should always use at least two-factor authentication. Each factor should be from different categories of authentication.
These categories include:
- Something you know (knowledge). Examples: password, PIN, passphrase
- Something you have (token). Example: smart cards
- Something you are (static biometric). Example: fingerprints
- Something you do (dynamic biometric). Examples: voice patterns, handwriting
So, for example, biometrics (such as fingerprints or facial recognition), one-time codes, or authenticator codes should be used in combination with your password. NIST guidelines, however, indicate that biometrics should be used in a limited capacity.
In addition, when choosing a password, people need follow these guidelines:
- The password is not in the dictionary, doesn’t have hints in it, and isn’t context specific. (For example, the password has part of the user’s name or username in it.)
- It's not reused on other websites. Reuse also means having a password that only differs by one character.
- It hasn’t been leaked. If a password has been leaked, they should never, ever reuse it.
- It’s stored properly. Passwords should be stored in secure places and should be encrypted.
- Is not easily guessable through social engineering.
- Does not include repetitive characters such as “aaa."
- Does not use known passwords. Passwords such as “password” should be avoided. Known passwords could also be passwords obtained from previous breach corpuses or dictionary words.
- The password is long. Length is more important than complexity.
Are there risks with using password managers to save your passwords? (e.g., LastPass, Google Password Manager)
Generally, it is a good practice to use secure and verified password managers. It helps users have longer passwords and avoid reusing passwords. However, as with anything, this can also be risky. Some password managers have been susceptible to breaches and leaks. It is important to know which password managers provide better security, have minimized risks, and learned from breaches. Google or Apple password managers are good options. There are also many other password managers that provide a good level of security.
Sachin Shetty, Ph.D.
Old Dominion University
How often should people change their passwords to ensure they are protected?
The frequency at which you should change your password depends on several factors:
- Use of unique, strong, complex and hard-to-guess passwords
- Use of two-factor authentication
- Use of a password manager
If these factors do not apply to you, then your passwords should be changed every three months or whenever the user is made aware of a password breach.
What are some best practices for people to avoid getting their passwords compromised or leaked?
As mentioned above, the best practices are:
- Create strong, unique, and complex passwords
- Never reuse passwords
- Use two-factor authentication
- Use a password manager
Are there risks with using password managers to save your passwords? (e.g., LastPass, Google Password Manager)
Password managers use encryption technology that ensures that only the user with the correct key or password to the password manager can access their passwords. Not even the companies that operate the password manager can access the user's passwords. So, you are only as good as the one single password you use to unlock your password manager. It's either best to always remember just one password or to use a biometric marker or face ID to unlock your password manager.
David Bader, Ph.D.
New Jersey Institute of Technology
How often should people change their passwords to ensure they are protected?
As a best practice, people should change their passwords every three months. This reduces the time that a compromised password will be used against you by a malicious actor.
What are some best practices for people to avoid getting their passwords compromised or leaked?
There are several simple things you can do to avoid getting your password compromised or leaked. First, when you create a new password, do not use any previously used passwords. Make sure your new password includes upper- and lower-case alphabetic characters, numbers, and special symbols (such as !@#$%^&*,.). [Do not use] any names or recognizable words.
There are several free or inexpensive password keepers on the market, and using one of these typically provides a secure vault for storing your passwords and autofilling them into your applications when necessary.
Are there risks with using password managers to save your passwords? (e.g., LastPass, Google Password Manager)
Really, there are no significant risks of using any of the popular password managers — just make sure to use a strong password to secure your vault, since that one password will protect all of your other stored passwords.
Daniel Ostergaard, Ph.D.
University of South Carolina
How often should people change their passwords to ensure they are protected?
Passwords should be changed frequently. Likewise, you really want to use different passwords for different applications. The sheer number of required passwords today presents a challenge to the average technology user, but the alternative of getting hacked or having your identity stolen is a high price to pay.
The fact is, there is a percentage of people out there who have not changed their passwords in years despite not realizing that the same password was hacked five years ago and has been circulating the dark web for years. The only safe approach today is to use completely different passwords and change them often. If you write the passwords down somewhere, you have opened up another possible weak point.
What are some best practices for people to avoid getting their passwords compromised or leaked?
The first might seem obvious, but don’t stick it to your computer with a sticky note. Likewise, do not write it down in a file with all your other passwords and save the file as, “Saved Passwords.” Hackers are far more sophisticated today than even a few years ago. Whether the bad actors originate from a nation-state or organized crime, the dark web is filled with passwords stolen from previous data breaches.
As the bad actors have honed their skills, so, too, have they honed their tools for “guessing” passwords. Hive Systems has developed an interesting table with estimated times it takes hackers to crack various password combinations. We know that a 12- to 14-digit password mixing capital letters, numbers, symbols, and letters can be much more difficult for a determined hacker. The days of using your anniversary, a child’s birthdate, or your mother’s maiden name should be well behind you.
Think of a verse from your favorite poem and then use the first letter from each word in the third sentence, mixed with symbols, numbers, and capitalization, and you’ll start to have a level of difficulty necessary in today’s security climate.
Are there risks with using password managers to save your passwords? (e.g., LastPass, Google Password Manager)
A question like this reminds me of the old maxim, “Don’t keep all your eggs in one basket.” Now, is it easy to use a password manager? Yes. Is it handy not to have to memorize a dozen different passwords? Yes. Are we safer using a password manager than not? Well, it depends.
Many password managers are protected by, yes, passwords. Relying on one single password to protect all your other passwords might be more convenient and efficient. However, as with most security precautions, being the most convenient or efficient has to be weighed with the potential damage if your passwords are compromised. This is highly dependent on a number of factors, including the difficulty of the password, how frequently it is changed, [and if it is] duplicated elsewhere, for example.
This is not to say that there are not some very good password managers out there. However, one must always consider a number of factors. Is there one correct answer for everyone? Well, if everyone could remember an alphanumeric password with 15 characters including random symbols and capitalization, then there would be no need for other resources. However, because each of us now has potentially dozens of passwords to use every day, the individual user must consider a range of risk factors to determine their own best course of action.
The practice of multiple passwords is still relatively new and we are still learning what best practices look like. For some people, having a password manager might be their best solution. For other users, it may not.
Answers have been slightly edited for clarity and brevity.
Tips for better password protection
- Use a password manager. If you're not currently using the best methods to store and manage your passwords, then switching to a password manager can help keep your accounts safe. Check out our guide to the best password managers.
- Protect yourself with a VPN. If you use public Wi-Fi networks regularly, then protect your data with one of the best VPNs.
Methodology
All About Cookies surveyed 1,000 U.S. adults on their password-keeping practices, as well as how they manage and share their passwords. Respondents had to opt in to the survey and were provided with a “Prefer not to answer” option for every question. All “Prefer not to answer” selections were excluded from relevant calculations.
-
Strong encryption and security
-
User-friendly interface
-
Free version is limited to one device at a time





