Advertiser Disclosure
All About Cookies is an independent, advertising-supported website. Some of the offers that appear on this site are from third-party advertisers from which All About Cookies receives compensation. This compensation may impact how and where products appear on this site (including, for example, the order in which they appear).
All About Cookies does not include all financial or credit offers that might be available to consumers nor do we include all companies or all available products. Information is accurate as of the publishing date and has not been provided or endorsed by the advertiser.
Editorial Policy
The All About Cookies editorial team strives to provide accurate, in-depth information and reviews to help you, our reader, make online privacy decisions with confidence. Here's what you can expect from us:
- All About Cookies makes money when you click the links on our site to some of the products and offers that we mention. These partnerships do not influence our opinions or recommendations. Read more about how we make money.
- Partners are not able to review or request changes to our content except for compliance reasons.
- We aim to make sure everything on our site is up-to-date and accurate as of the publishing date, but we cannot guarantee we haven't missed something. It's your responsibility to double-check all information before making any decision. If you spot something that looks wrong, please let us know.
From work to school to leisure, people use the Chrome browser because it connects to their Google accounts. Kids are using it with Google Classroom. People use it for work when their companies use Google Workspace. It’s built for speed, which is why users like it.
Unfortunately, cybercriminals are the reason we can’t have nice things. To hide their malware, they created the Chrome.exe virus, also known as the Poweliks trojan. Because the malware appears to be a real application, you don’t realize your device has been infected.
This type of malware is the cybercriminal version of Obi-Wan Kenobi telling Stormtroopers, “These aren’t the droids you’re looking for.” You can expect to see the Chrome.exe process in your Task Manager if you are using the Chrome browser. Meanwhile, the Chrome.exe that’s running is really the malware you want to remove.
To remove Chrome malware, such as the Poweliks trojan, you should install a highly-rated antivirus program that scans your device and quarantines the infected process. Keep reading our Chrome.exe virus removal guide for step-by-step instructions.
How to identify the Chrome.exe virus
How to remove the Chrome.exe Virus
How to avoid malware
Chrome.exe FAQ
Bottom line
What is the Chrome.exe virus?
The Chrome.exe virus, or Poweliks trojan, is a Trojan horse malware that disguises itself as a legitimate computer program to evade detection. The ".exe" means it's an executable file. When someone clicks on the file, it gives the computer instructions about what to do next.
When a user clicks on the file to open it, it triggers a series of actions:
- The Poweliks downloader installs on the device.
- The Microsoft Windows registry stores the file under the name Chrome.exe.
- The installer deletes itself.
Because the malware, disguised as Google Chrome, installs in the Windows registry and not the hard drive, antivirus tools have a hard time detecting it.
Once installed, the virus can:
- Read your emails
- Access your phone contacts
- Establish connections with hidden websites
- Create, modify, or remove files or processes
- Collect and send system information
- Perform click fraud, or generate multiple clicks on advertisements to generate more revenue
- Download additional malware
- Be controlled by a cybercriminal
How to identify the Chrome.exe virus
Although the trojan malware “Jedi mind trick” can sound scary, you can still use Chrome without worrying too much. By understanding the difference between how the legitimate Chrome.exe and the Poweliks Chrome.exe virus work, you can identify a virus infection and keep using your favorite browser.
What is your computer doing?
Poweliks uses the same name as your browser’s executable file, but your computer will act differently. You can look for the following symptoms to diagnose your computer with the virus:
- Your computer is slow.
- You see a lot of popup ads when browsing.
- You see ads from websites you’ve never visited.
- You can’t access websites.
- Your browser won’t let you download files.
How much memory is your browser using?
Just like you need to check for symptoms that differentiate strep and the common cold, you want to look for additional digital symptoms to determine whether your computer has a dangerous infection. Some other indicators of the Chrome.exe virus might include high CPU usage along with:
- Look in your Windows Task Manager to see what programs are running and look for Chrome.exe*32.
- You may see more than one version of the Chrome.exe file. This is the first hint that your computer is infected.
- Review the Memory column in Windows Task Manager for Chrome.exe*32.
- If you have a lot of tabs open, close them to see if that reduces the amount of memory Chrome uses.
What processes should you look for?
If Chrome is still taking up a lot of memory, now you need to start thinking about the final definitive test. Just like you’d go to the doctor to get a throat culture for strep, it’s time for you to take a definitive look at your device. Although Poweliks looks like Chrome, it has some unique characteristics. Going back to your Task Manager, you need to look for the following processes:
- dllhost.exe *32
- dllhst3g.exe *32
- DLLHOST.exe
- dllhst3g.exe
What other files should you look for?
Finally, you might want to search your file folders for Chrome.exe*32. To do this:
- Open your Task Manager.
- Right-click on the Chrome.exe*32 process.
- Open the file location.
The only file location where you should find the Chrome.exe*32 file is this directory:
C:\Program Files (x86)\Google\Chrome\Application
If you find the file anywhere else, you have a Poweliks infection.
How to remove the Chrome.exe Virus
Although it might take you some time to locate the Chrome.exe virus, you don’t need to buy a new device. You can remove the virus by taking the following steps.
1. Install and update antivirus software
The Chrome.exe virus is just the beginning of the problem. With malware like Poweliks, you have to worry about the additional malware that it downloads, launches, and updates. With all these other files, you either need advanced IT skills or antivirus software to help you.
Finding the best antivirus software for your needs is the first step. Although most antivirus should be able to detect Poweliks, the following have specific detections for it:
Bitdefender
-
Antivirus software offering reliable security
-
Simple yet powerful interface tools
-
Perfect protection score in third-party tests
-
Premium features incur additional subscription fees
With excellent protection scores, friendly customer service, and a full range of security features, Bitdefender is a great choice for protecting your device from malware. When we tested it, it had no impact on our system performance.
Get Bitdefender | Read Our Bitdefender Review
McAfee
-
All-in-one protection for your personal info and privacy
-
Excellent antivirus protection
-
Additional features like a file shredder and parental controls
-
Multiple pop-ups for text notifications can be annoying
A well-known and well-regarded name in the antivirus industry, McAfee also scored well in third-party protection tests. Along with a firewall, it also includes phishing protection, parental controls, and a file shredder. We especially like that its cheapest plan, Antivirus Basic, is still packed with a firewall, password manager, VPN, and identity monitoring.
Get McAfee | Read Our McAfee Review
Malwarebytes
-
Free version with manual scans
-
Near-perfect protection scores for Premium plan
-
High starting price point for paid plans
For those using a Windows PC, Malwarebytes is worth a look. Its no-frills approach means it costs less than some other antivirus programs — but you still get strong malware protection. And if cost is your biggest hurdle, Malwarebytes offers a free plan with manual antivirus scans. As we always say, some protection is better than no protection.
Get Malwarebytes | Read Our Malwarebytes Review
ESET
-
Lots of useful features
-
Offers a 30-day free trial with no credit card required
-
Lackluster customer service options
If you're not a fan of a barebones approach to malware protection, ESET's wide range of features might appeal to you. Using advanced machine learning, it protects your devices from phishing attacks, malware, fraud, and ransomware. It also comes with anti-theft protection for your device — a definite plus if you travel with your laptop.
Get ESET | Read Our ESET Review
2. Run an antivirus scan
After downloading an antivirus program or antimalware tool, you need to run a full system scan. To do this, you should:
1. Open the solution’s dashboard or main window.
2. Look for System Scan.
3. Click Start Scan.
4. Once the antivirus completes the scan, you can review the report that looks like this:
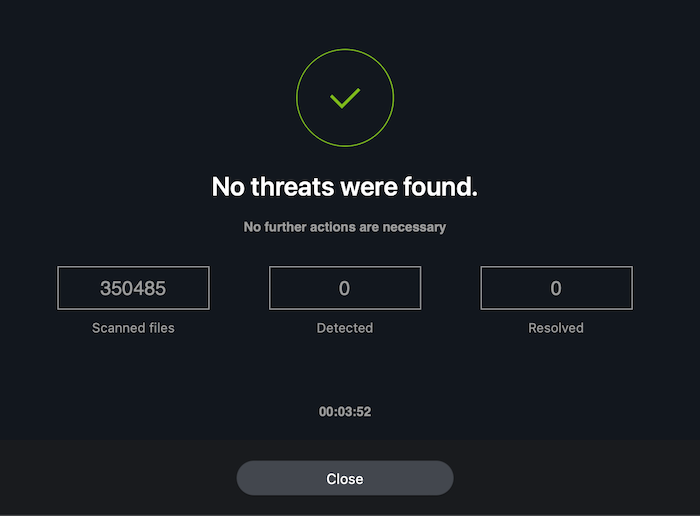
3. Delete corrupted files
Your antivirus will automatically quarantine the virus’s files. Many will also delete them, but if yours doesn’t, then you may want to find a malware removal tool that works with your operating system. For example, Malwarebytes works with both Mac and Windows operating systems, so if your household has devices running both, this is a good option for you.
These solutions usually delete all the corrupted files for you. For example, in Malwarebytes, you would see this type of report:
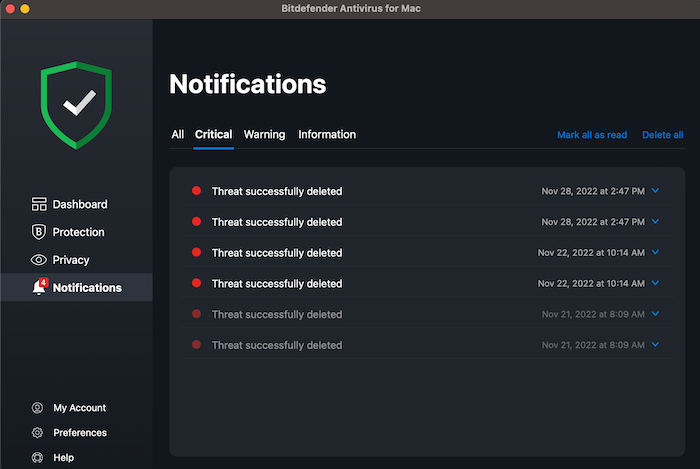
4. Restart your computer and scan again
Finally, as you would on a math test, double-check your work. Cybercriminals don’t want you to be able to remove their malware, so they build persistence into them.
Restarting your computer stops all processes, cleans up your device’s memory, and clears out the cache. You want to make sure that you’re starting with a clean slate after you remove the malware.
Because malware processes automatically start running as soon you log in, doing one more antivirus scan ensures everything is cleaned up.
To uninstall unwanted adware on Windows 7, 10, or 11, open your Control Panel > Programs and Features > Uninstall a program and select the program you want to remove.
How to avoid malware
Just as taking your Vitamin C helps your immune system protect you against colds and strep, you can also take steps to protect your information and devices. Learning how to stay safe online is the protective vitamin for your digital health.
Update your devices and software
In the case of Poweliks and other downloader malware, the danger lies in its ability to control the device and install other malicious software. Typically, malware takes advantage of vulnerabilities, the weaknesses in an operating system or software’s code.
Software and operating updates fix these weaknesses, so installing security patches is a critical cybersecurity step.
Secure your wireless network
By securing your wireless network, you can protect your devices from different types of attacks, including malware. To secure your network, you can edit your router’s settings to:
- Encrypt it using Wi-Fi Protected Access 2 (WPA2).
- Change the default password.
- Update firmware to protect against vulnerabilities.
- Scan your router for malware.
You should also consider using a virtual private network (VPN) to further secure your Wi-Fi connection — especially if you connect to public Wi-Fi. A VPN makes it harder for hackers to target your device with malware by disguising your IP address. During our testing, these top VPN apps stood out from the rest:
The best VPN apps for securing your Wi-Fi network
| VPN |  NordVPN |
 Surfshark |
 Private Internet Access |
| Starting price | $2.99/mo | Starts at $1.99/mo | Starts at $2.03/mo |
| Number of devices | 6 | Unlimited | Unlimited |
| Server count | 5,000+ in 60 countries | 3,200+ in 100 countries | 84 countries + 50 U.S. states |
| Streaming support | |||
| Torrenting support | |||
| Learn more | See NordVPN Pricing | See Surfshark Pricing | See PIA Pricing |
Be careful when downloading files
Poweliks is called a fileless malware because it installs in the registry instead of the system. However, cybercriminals typically hide the malware in malicious documents either sent by email or downloadable from a malicious website.
To protect against the Chrome.exe virus, you should only download attachments or files when you can trust the sender or website.
Change your passwords
To protect yourself, you should have a unique password for every login. After you delete any malware from your device, you should reset all your passwords. Some malware, such as Poweliks, can download and install a virus that steals usernames and passwords.
Use an antivirus
When you install antivirus software on your device, it regularly scans for, detects, and deletes malware. With this protection, you don’t have to worry about looking for signs that a virus infected your device.
Even Macs and Chromebooks should have some form of antivirus protection. If you're missing this key form of protection, check out our guide to the best antivirus software for recommendations.
Chrome.exe FAQ
Is Chrome.exe a virus?
Chrome.exe is the name of the Chrome browser software file. However, the Poweliks virus, also called the Chrome.exe virus, uses the same name as the legitimate software file to hide in a computer’s registry.
What is the Poweliks Trojan?
The Poweliks Trojan, also called the Chrome.exe virus, is a malware that disguises itself by stealing the name of the Chrome browser. Poweliks is a fileless malware, which means it installs in a device’s registry rather than the hard drive. By hiding in the registry, it’s more difficult to detect, which allows it to continue to download and install other malware or send information to cybercriminals.
Why do I have so many chrome.exe in my task manager?
Chrome creates a separate process for each tab, extension, utility, and subframe. It runs multiple processes for each tab, utility, and extension so if the browser or tabs crash, the user doesn’t lose any data.
Can Chrome get a virus?
The Google Chrome browser is a software that can get a virus. The Google Chrome virus is a browser hijacker malware that changes settings and configurations without the user’s permission. Signs of infection include:
- Pop-up ads
- Redirects to suspicious websites
- Changes to the homepage
- Browser setting changes or deletions
- Suspicious browser extensions
To remove the virus, you should:
- Open Chrome.
- Click on the three dots in the top right corner to open the drop-down menu.
- Scroll down to Settings.
- Once in settings, go to Advanced > Reset and clean up.
- Click Clean up computer and select Find harmful software.
- Delete any malicious programs found in the browser.
Bottom line
For most people, a virus like Poweliks can feel overwhelming. However, the good thing about technology is that you don’t have to be an IT expert to fix most things. When you have a good antivirus and learn about online safety, you can prevent most cyber dangers and continue to do everything you enjoy online.
-
All-in-one protection for your personal info and privacy
-
Excellent antivirus protection
-
Additional features like a file shredder and parental controls
-
Multiple pop-ups for text notifications can be annoying