Advertiser Disclosure
All About Cookies is an independent, advertising-supported website. Some of the offers that appear on this site are from third-party advertisers from which All About Cookies receives compensation. This compensation may impact how and where products appear on this site (including, for example, the order in which they appear).
All About Cookies does not include all financial or credit offers that might be available to consumers nor do we include all companies or all available products. Information is accurate as of the publishing date and has not been provided or endorsed by the advertiser.
Editorial Policy
The All About Cookies editorial team strives to provide accurate, in-depth information and reviews to help you, our reader, make online privacy decisions with confidence. Here's what you can expect from us:
- All About Cookies makes money when you click the links on our site to some of the products and offers that we mention. These partnerships do not influence our opinions or recommendations. Read more about how we make money.
- Partners are not able to review or request changes to our content except for compliance reasons.
- We aim to make sure everything on our site is up-to-date and accurate as of the publishing date, but we cannot guarantee we haven't missed something. It's your responsibility to double-check all information before making any decision. If you spot something that looks wrong, please let us know.
WebRTC is truly a double-edged sword. On one hand, WebRTC technology makes it possible to talk to the people we work with and care about quickly and seamlessly over any web browser. On the other hand, it poses a significant security risk to anyone who uses it.
In this article, we’ll explain what a WebRTC leak is and how you can actively protect yourself against it with one of the best VPNs or by turning off WebRTC on your browser.
What is WebRTC?
How to complete a WebRTC leak test
How to block WebRTC leaks
WebRTC FAQs
Bottom line
What is a WebRTC leak?
A WebRTC leak is a security vulnerability that can occur when you use WebRTC-based applications, like Facebook Messenger or WhatsApp, on your internet browser. In order for WebRTC technology to work properly, your IP address gets exposed by default as part of the process.
Although using WebRTC technology has become normalized out of convenience, having your IP address exposed increases your risk of being a victim of cybercrime and privacy invasions.
WebRTC leaks can happen on any web browser and on any type of device.
Why are WebRTC leaks bad?
WebRTC leaks are problematic because they can expose your local IP address, leaving your online privacy and safety more susceptible to bad actors.
These leaks are especially concerning if you’re already using a virtual private network (VPN), as they indicate that your VPN server is not doing its core job of protecting your anonymity online.
Having your IP address land in the wrong hands can put your safety and well-being at serious risk. When your IP address is exposed or traceable, any of the following can occur:
- Criminals may find your device’s location. This is especially problematic if you broadcast what city you’re in on social media sites like Instagram or Facebook. A criminal can use your IP address to locate your device and trespass onto your property or otherwise harm you.
- You could fall victim to a DDoS attack. DDoS attacks, or Distributed Denial of Service attacks, can start with hackers finding your IP address. The hacker prevents you from accessing the internet, thus causing a disturbance to your day-to-day affairs.
- Hackers may impersonate you and conduct fraudulent activity on your behalf. Your IP address can be used as a starting point for hackers to uncover more of your personal information. Once they’re armed with login information or specific details about your online activity, purchase habits, or services you subscribe to, they can use it to commit fraud and identity theft.
You may see that you have both an IPv4 and an IPv6 address, but what does that mean?
- IPv4: This is the original version of Internet Protocol (IP) created in 1983. It can store more than 4 billion addresses and carries about 94% of internet traffic today.
- IPv6: The most recent version of IP, IPv6 was created in 1994 and is still being enabled to fix issues with the original IPv4 version. IPv6, sometimes called IPng, can store about 340 undecillion addresses (340 plus 36 zeroes).
What is WebRTC?
WebRTC stands for Web Real-Time Communications. WebRTC technology enables real-time voice and video connections to be established through your web browser. It does this by communicating with the website or app you're using and exchanging information like your local and public IP addresses.
Examples of common services that use WebRTC include:
- Discord
- Facebook Messenger
- Google Meet
- GoToMeeting
- Snapchat
Your public IP address is assigned to your router by your internet service provider (ISP). It’s safer to share this online, since your public IP address is traced back to your ISP. This could reveal your geographic location, but not your exact address.
A local IP address, also called a private IP address, is assigned to each device you use to connect to the internet. This allows your devices to talk to each other over your home network — but anyone not on your home network can’t communicate with your devices. Local IP addresses are traceable, but only by devices that are also on your home network.
How to complete a WebRTC leak test
In addition to letting you stream Netflix, your VPN should be able to shield your real IP address from potential harm, no matter the circumstances. The results of your IP leak test will help you determine how well your VPN is doing its job. Here’s how to perform a WebRTC leak test:
- Disconnect from your VPN service and make sure it’s turned off, closed out of, etc.
- Check your IP address by typing what’s my IP into your browser bar or visiting WhatsMyIPAddress.com. Your internet service provider (ISP) will show you your IP address. Write it down in a safe place.
- Close your browser window and application.
- Reconnect to your VPN.
- Go to a leak checker website to see if your IP address is still visible. We recommend trying a few different ones, like BrowserLeaks.com and Hide.me, to be as diligent and thorough in your testing as possible. If you can still see your IP address, your VPN is not protecting you against leaks. If it’s not there, your information is still safe.
If you find your VPN doesn’t prevent WebRTC leaks after testing, you’ll need to either get a different VPN or block WebRTC from your browser manually.
How to block WebRTC leaks
The easiest way to block WebRTC leaks is by using a VPN. Unfortunately, some VPNs still allow WebRTC traffic to bypass the encryption tunnel, thus defeating the purpose of using it in the first place. That’s why we strongly recommend performing a leak test even if you’re already using a VPN.
If you find your current VPN is susceptible to leaks or are looking to use one for the first time, here is a list of trusted VPN providers that all passed our WebRTC leak test:
- NordVPN: Nord offers one of the best-known VPNs for plenty of good reasons. Along with passing our WebRTC leak test, it also passed our DNS leak test, uses military-grade encryption, and offers double VPN, which adds more security to your browsing data and location.
- ExpressVPN: ExpressVPN offers top-notch security standards, which could justify its premium price. It has a strict no-logs policy that has been independently audited and a speedy and secure protocol called Lightway for an enhanced browsing experience.
- Surfshark: If you're looking for a VPN to cover all your devices, then Surfshark is among the best for its value. It allows for unlimited simultaneous connections and offers compatibility for most operating systems, smartphones, routers, and even smart devices.
You can also block WebRTC leaks manually by disabling WebRTC technology on your web browser, and you don’t need to be a tech expert in order to do so successfully.
Some browsers even allow you to use plugins and addons to block WebRTC leaks for you. We’ve provided the exact steps on how you can disable it on Chrome, Firefox, Safari, and Microsoft Edge for your Windows PC, Mac, iOS, or Android device.
-
High-quality VPN offering safety and speed
-
Loads of servers for multiple connection options
-
Works with popular streaming services, including Netflix
-
Too many confusing plans
How to turn off WebRTC on Chrome
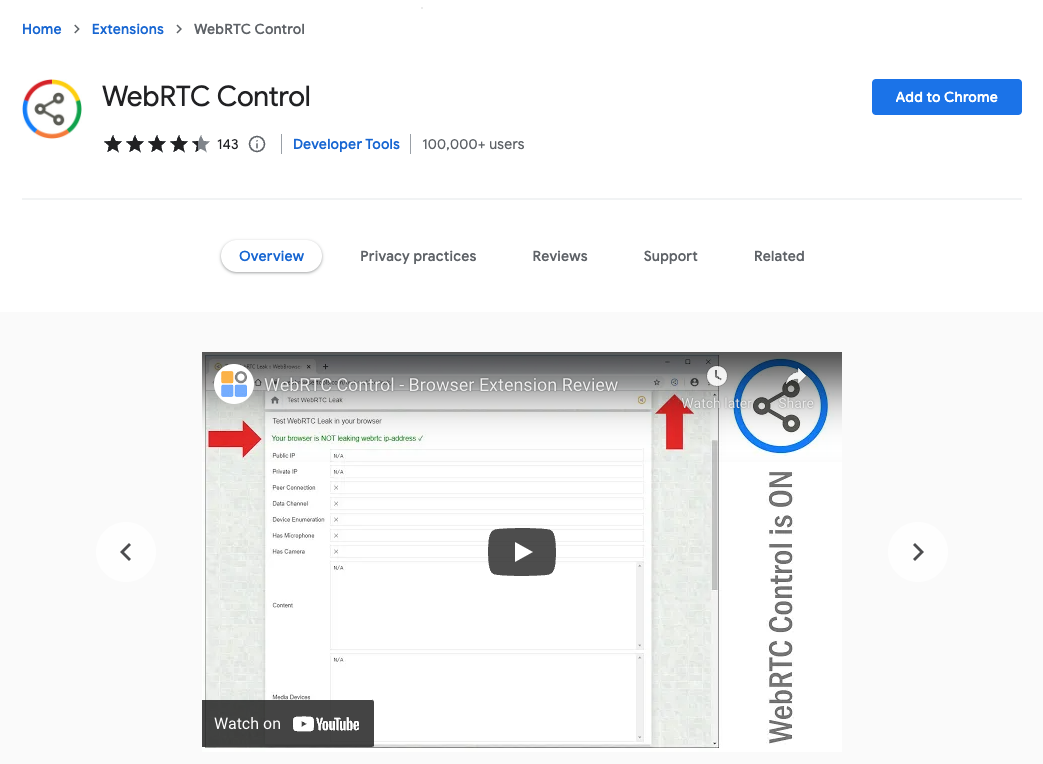
The best way to turn off WebRTC capabilities on your Google Chrome browser is to install a browser extension. Here are some popular and reputable extensions that will help you stop WebRTC leaks:
To install any of the Chrome extensions listed above, click on the hyperlink we included to visit its product page. When you’re ready to install one, click the blue button that says “Add to Chrome.”
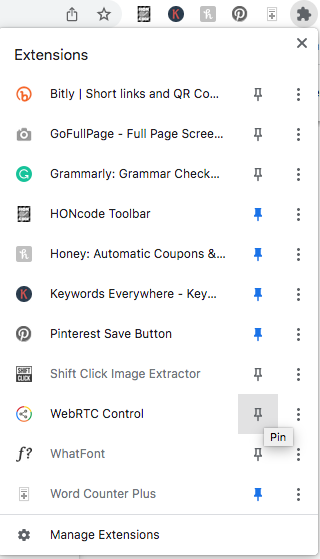
Next, pin the extension’s icon to the top of your browser for easy and immediate access. Click on the jigsaw puzzle piece towards the top right corner of your screen, then click on the push pin icon that appears next to your WebRTC blocker.
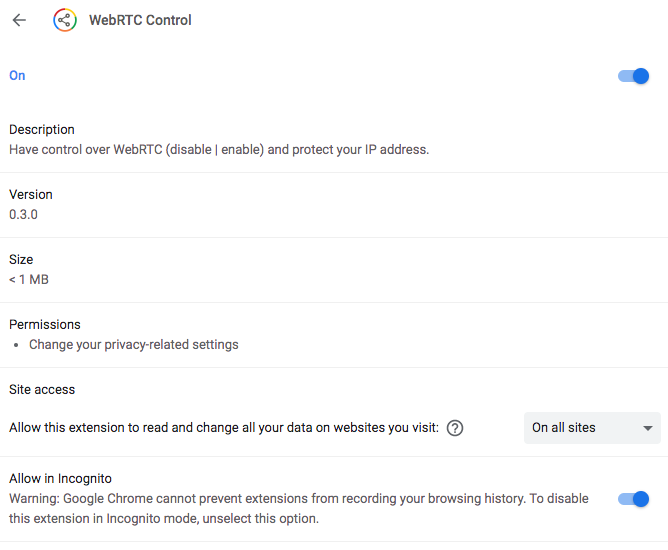
You’ll also need to ensure that WebRTC leaks are blocked on Incognito mode. By default, most extensions are turned off for Incognito mode.
To activate your WebRTC extension in Incognito mode, type chrome://extensions/ into your browser bar. Under the name of your WebRTC extension, click on “Details.” Toggle on the switch next to “Allow in Incognito.”
Since Opera and Brave both use the same Chromium engine as Google Chrome, you can use many of the same browser plugins. That means you can follow the same steps above for preventing WebRTC leaks on Chrome even if you use Opera or Brave.
How to turn off WebRTC on Mozilla Firefox
On Firefox, you can disable all WebRTC services without using an extension. Follow these steps exactly and you’ll be protected from future leaks.
- Type about:config into the address bar and hit enter (or return if you’re using Apple hardware). A warranty warning will then appear on your screen. Once it does, click on “Accept the Risk and Continue.”
- On the next screen, click on “Show All.”
- A long list of settings should appear on your screen. We strongly advise against touching these, as they could interfere with your browser’s performance. Search for “media.peerconnection.enabled” to get to the setting you need to adjust.
- You’ll see that it’s currently set to “true.” To turn off WebRTC, you need to set it to false. Click on the toggle button all the way to the right of your screen.
- Close your browser and reload it to make sure the changes take effect.
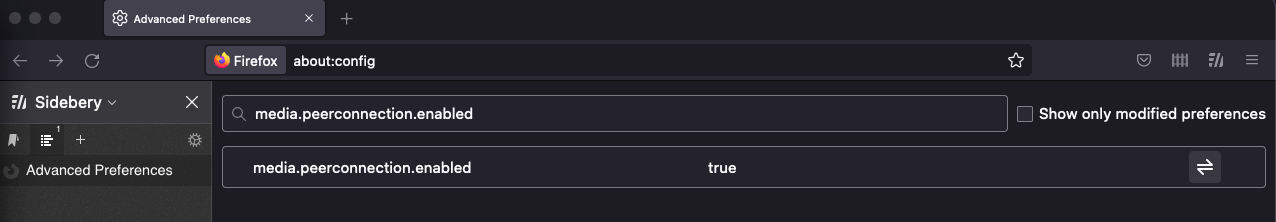
That’s all it takes. Keep in mind that this disables any website that uses WebRTC technology, so services like Google Meet and Facebook Messenger may not let you take video or audio calls through your browser anymore. Be sure to plan accordingly.
How to turn off WebRTC on Safari
If you use Safari as your default browser, it’s easy to turn off WebRTC. All you need to do is the following:
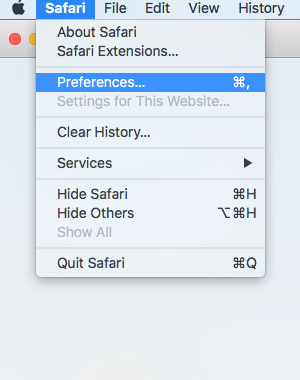
1. Open Safari and hover your mouse under “Safari” at the top left corner of your screen. On the dropdown menu, click on “Preferences.”
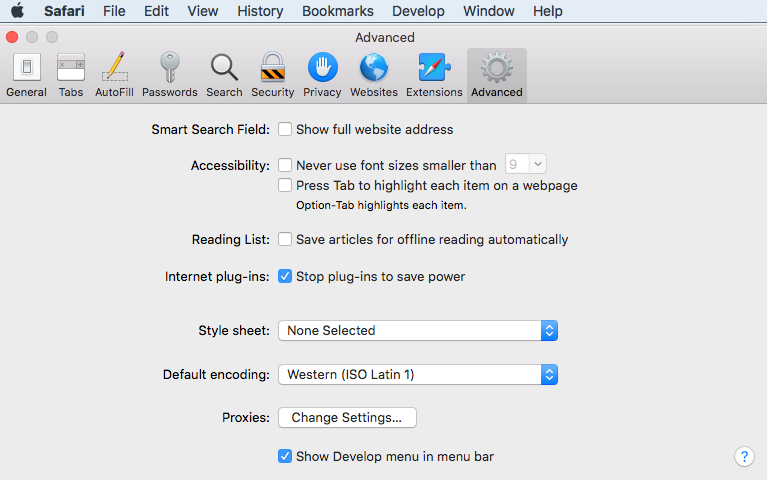
2. On the window that pops up, navigate to “Advanced.” Check the box that’s next to “Show Develop Menu in Bar.”
3. A new “Develop” tab should appear at the top of your screen once the box is checked. Click on the “Develop” tab and hover your mouse over “Experimental Features.”
4. See if there is a checkmark next to “WebRTC mDNS ICE candidates.” If yes, click on it to disable WebRTC.
5. Close your browser and restart it to start browsing safely.
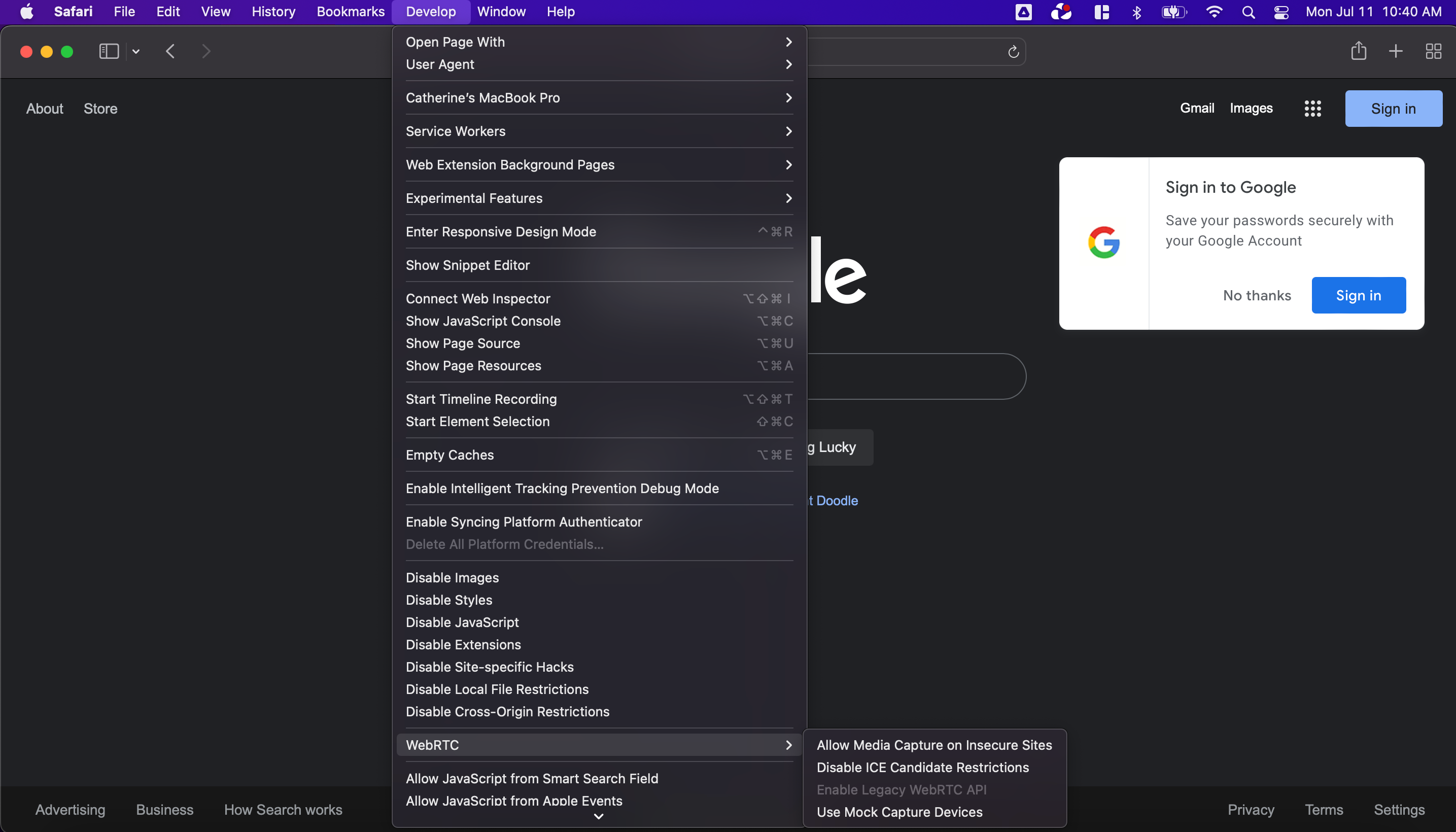
Once you’ve completed these steps, you should be all set with preventing WebRTC leaks on Safari.
How to turn off WebRTC on Microsoft Edge
Unlike Firefox and Safari, Microsoft Edge does not let you disable WebRTC technology entirely. Instead, some versions let you hide your IP address when you’re using websites and services that use WebRTC. This means you can continue to use WebRTC applications normally without revealing your IP address. Here’s how to hide your IP address:
- Type about:flags into the address bar and press enter.
- Check the box next to “Hide my local IP over WebRTC connections.” This box is usually unchecked by default.
- Close your browser window and reload it.
Microsoft Edge makes it uncomplicated to stay safe when browsing the web.
Don’t see the “Hide my local IP” setting?
You’re not alone. This could be due to a July 7, 2022, Microsoft Edge update that addressed two WebRTC zero-day exploits. The most stable, up-to-date version is 103.0.1264.49.
If your Edge browser version doesn’t match or if you have updates available, be sure to download and install them for the latest security patch.
WebRTC FAQs
How do I stop a WebRTC leak?
You can stop a WebRTC leak one of two ways: by using a high-quality, trusted VPN or by disabling it in your browser manually.
What is a WebRTC leak test?
A WebRTC leak test is a series of steps to determine whether or not you’re vulnerable to WebRTC leaks. WebRTC leak tests can be performed quickly and at no cost, whether you’re using a VPN or not.
Is it safe to disable WebRTC?
Yes, it’s completely safe to disable WebRTC. Doing so, however, may mean that websites that use WebRTC technology will stop working.
Bottom line
A WebRTC leak can reveal your IP address, putting your privacy and safety at risk — even if you use a VPN. Not all VPNs are created equal, so checking for potential leaks is critical in order to have total peace of mind when browsing the web.
Thankfully, you can safeguard your privacy by using a tried and true VPN like NordVPN or by disabling in-browser WebRTC yourself. Whichever method you choose, we also highly recommend staying vigilant for new updates to better protect yourself against digital threats.
-
High-quality VPN offering safety and speed
-
Loads of servers for multiple connection options
-
Works with popular streaming services, including Netflix
-
Too many confusing plans